Which of these are Identity and Access Management acronyms? Phonetically for Finnish speaking people these are different kind of sounds of chimes. But trust me, two of these are IAM thingies as well (1.
This article tries to explain new terms in the field. You need to read ahead to find out correct answer.
Climb the IAM stairs
I have learned from the best. The method of illustration is mimed from amazing works I’ve seen before from others (2.
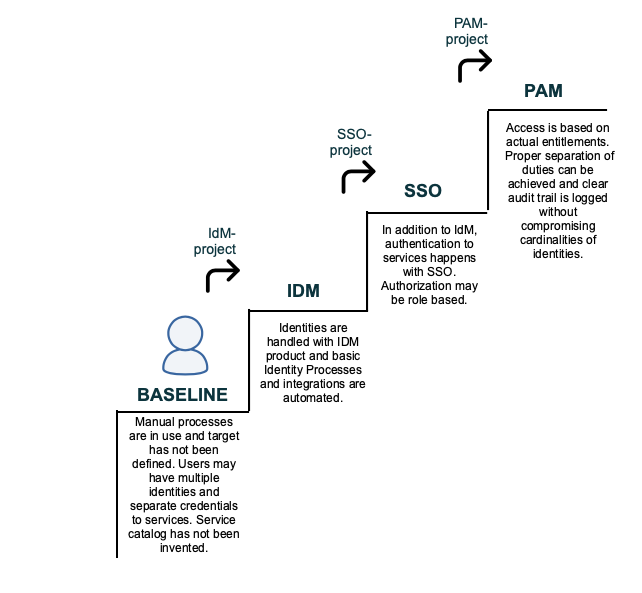
The illustration IdM Stairs tries to draw a picture of how an example organization might progress in improving the processes and services regarding identities. Illustrated steps are only an example of a typical evolution. Baseline of organizations differ and priorities to improve overall IT Service Management differ.
Traditionally organizations acquire an IdM system when they find that processes regarding Identity Management flows are laborious. After a while being satisfied with the new comfort of automatization, users start to complain about entering the difficult password again and again. Then, a new Single Sign On (SSO) system is taken in use. In more progressed organizations even federated authentication will be taken in use. The more bold even will federate their Identity Provider making it possible to cross organizational borders.
Privilege is an intriguing term
According to Wikipedia: ”A privilege is a certain entitlement to immunity granted by the state or another authority to a restricted group”.
It is not a new phenomenon that people in IT like to invent new terms to things. Traditionally, in the field of authorization, the term entitlement has been more popular. Semantically, the term privilege overloads the term entitlement in that it is something that is desired and requested where as entitlement is more of a thing that is provisioned regarding to e.g. a duty that has been handed to a person.
So, you could substitute the new popular term Privileged Access Management with the traditional term entitlement management joined with access management.
Access Management has evolved as well
I had an interesting discussion lately. A debater argued that our idea was the same as giving a root access to anyone. In past that would’ve been a hideous thing to do. I didn’t, but I would’ve wanted to say that exactly, you are correct in your metaphor in that it is exactly what we want to do. We want to give the root access to anyone that has the privilege.
The root access for anyone has traditionally been a hideous thing in that we wouldn’t have been able to know who had been the actual person to have access. However, lately the security people have been protecting the access to assets according to onion defense.
The idea is that you don’t even need to protect the inner core of your assets with the best artillery. You should put the strongest artillery defending the outer wall and then you can ease the access while penetrating deeper inside the walls of your onion. An important thing for you to do is to write logs of every access event. Put the logs to a secure place, somewhere you trust the most.
Then you don’t need to be afraid of giving root access. What ever happens, you know that the users that had access were privileged (or entitled, if you like) and you can track every move they did (taken that the surveillance was done according your privacy policies).
PAM puts this together
Yes, now you have it. PIM and PAM are the terms that refer to Identity and Access Management. POM is only the sound we the Finnish people hear when the big bell of a church bell is being played.
With the term Privileged Access Management (PAM), the market refers to a product that is able to secure people’s access to the protected assets. It may be able to monitor, trace and record access or even traffic and write audit trail logging of events.
With the term Privileged Identity Management (PIM), the market refers to a product that is evolved from the traditional Identity Management service. Usually the difference is that the decisions in authorizations are made Just In Time (JIT). That is, authorities are not decided in advance, like in traditional Identity Management. Traditionally the decisions would’ve been made according to a role or to a position in the organization. However, PIM can handle the decisions e.g. time bound, based on a request and overall, based on what the user actually needs authority to do at that point in time.
PIM-products also gather and report information and raise alarms about granted events possibly in co-operation with the PAM-product. They may have tools to analyze gathered data and store, search and display audit trail of events or this task may be handed to a SIEM-product.
In some products features interleave so that you cannot clearly see where PIM ends and PAM begins or the other way around.
Acknowledgements
- To fully acknowledge and credit the title; the title also refers to a title of childrens’ book from author Els Stam. It seems to be a rare book that is difficult to access. If you happen to have a copy, would love to read it. (Pim, Pam en Pom en de stoute reus, Els Stam)
- Federoidun identiteetinhallinnan periaatteet, Mikael Linden (https://docplayer.fi/1406387-Federoidun-identiteetinhallinnan-periaatteet.html)

