Identity and Access Management (IAM)
WeAre provides services around digital identities, from mapping the current state, modernising thinking patterns and streamlining processes to technical development and maintenance of implementations.


What does Identity and Access management include?
Identity and Access Management (IAM) covers identity management (IdM) as well as access rights and control. Identity lifecycle management and the synchronization of identity information connects together people, information, devices, and systems (entities). Access control ensures that only authorized entities can access other destinations in a timely manner and regardless of location or terminal.
Expert Services
There are many ready-made identity providers on the market, that suit the common authentication use cases of most organisations. WeAre's experts are ready to help in selecting the best suited product, technology, and solution for your specific needs.

Mapping and planning of the current state
Covers the mapping of existing identity management systems and their use, the imaging of processes in situations where they have not been considered, and the readiness of existing systems to be used in accordance with our concept. Extensive planning enables process imaging of identity and access control entities and defining of user lifecycle management.
Deployment project
In a situation where the customer’s current state and target state are already clear, we are happy to help our customers enable practical implementations, both at the technical level and in the roles of project management. Our work history ensures a multidisciplinary mindset and gap analysis process at a level that ensures the end result is functional, enables future change factors and, if necessary, meets strict regulatory requirements or other required compatibility criteria.

Continuous support services
Once the project is completed, we will help maintain the functionality of the systems, make changes to them if needed, and expand the entities to cover new needs. We are involved in supporting and strengthening the client's own set of identity management experts, or helping in training and familiarising the team from the start.
Olevi - Se helppo suomalainen tunnistuspalvelu
Olevi is a service that implements OpenId Connect (OIDC) and SAML2 authentication policies, which identifies users and enables them to access systems and applications.
Olevi is an innovation that started at WeAre. WeAre acts as Olevi's authorized reseller and support service partner.
Identity Provider, is a service that implements OpenId Connect (OIDC) and SAML2 authentication policies that identify users, enabling them to access systems and applications. IdP can be used to implement Single Sign On (SSO), which allows a user to access all authenticated applications based on a single authentication transaction without separate authentication. IdP connects to authentication methods as needed. WeAre has implemented an authentication proxy model that relies on existing OIDC authentication sources (e.g., Azure AD, Google, Facebook, etc.). The user information generated by the authentication methods can be enriched from other sources, such as the organisation’s IdM system. IdP is implemented with open source Shibboleth Identity Provider software.
IdP connects to authentication methods as needed. WeAre has implemented an authentication proxy model that relies on existing OIDC authentication sources (e.g., Azure AD, Google, Facebook, etc.). The user information generated by the authentication methods can be enriched from other sources, such as the organization’s IdM system.
IdP is implemented with open source Shibboleth Identity Provider software.
Enrichment of identification
It is possible to implement phases to the identification process, in which the user identification information obtained from the identification method is enriched with user data from external sources. For example, if a customer's user authentication is based on the Azure AD authentication service, but the user role information is stored in a separate system, the role information can be retrieved from another system (e.g., CRM) after the actual authentication event and then added to the authentication response. The decision on user access to the application can be made based on the role information.
The enrichment of authentication information in connection with an authentication event saves the implementation of a separate synchronisation to the service, as the user role is handed over during the authentication event.
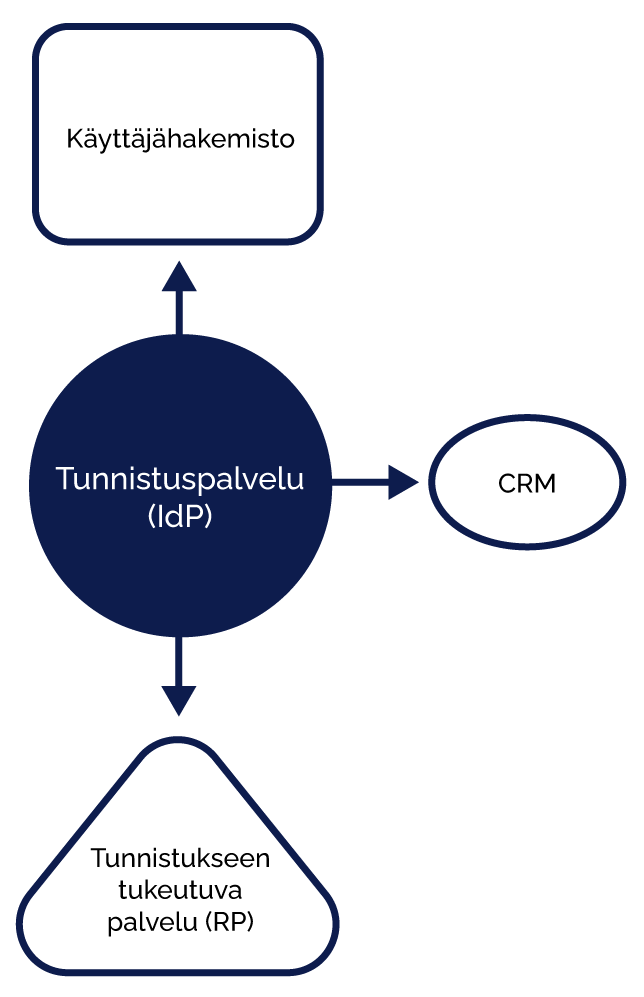
Identification adapter
The customer may have an identity provider service in use, which is not compatible with a system in use, that relies on authentication. Typically, the client has a SAML2 authentication solution, but the service has implementations for only OIDC-based access control. Or the case may be the other way around.
The authentication service can act as an adapter, i.e. an intermediary, where the authentication method is adapted to the service in the form for which it has ready-made solutions. Even the very unique and hand-tailored services can often be protected by authentication, even if they were not initially implemented with a single sign-on method or with connections to modern authentication protocols.

Looking to contact us?
Send us a message and we will be in touch.
Contact Form

No Visibility into your Critical Business Processes? Here’s what you need to do.

Case Study: Modernizing Survey Analytics with Cloud-Native Observability
The Power of Observability and AIOps in Complex and Modern IT Operations

How to Set Up a New Observability System: Key Steps and Measures

Optimizing Data Management with Observability: Prevent Failures & Scale Smartly
Harnessing LLMs Securely: Challenges, Innovations, and Splunk’s Role
Blog posts

Tunnistaminen kansalaisten ja loppukäyttäjien näkökulmasta
Tunnistaminen on aihe, josta jokaisen tulisi puhua enemmän, eikä vain tietomurtojen yhteydessä. Tämänkertaisessa jaksossa käsitellään tunnistamista kansalaisen ja loppukäyttäjän näkökulmasta.
Vieraana jaksossa Suomen Tunnistautumisosuuskunnan eli Sinunan toimitusjohtaja Mikko Nurmi.
Mikä on tietoturvaseteli? Näin se toimii
Tietoturvaseteli on valtioneuvoston antama asetus tietoturvan kehittämisen tuesta, joka tuli voimaan 1.12.2022. Määräaikaisen tuen avulla yritykset voivat parantaa järjestelmiensä tietoturvaa.

Tunnistuspalvelu on kustannustehokas ratkaisu identiteetinhallintaan
Jos olet pyrkinyt löytämään kustannustehokkaan ratkaisun hankalaan identiteetinhallinnan ongelmaan, olet todennäköisesti huomannut, ettei sellaisia ole juuri saatavilla.

OpenID Connect claimien arvojen tulkinnoissa on eroja
Asiakkaan tunnistusratkaisun toteuttamisen yhteydessä teimme äskettäin havainnon:
Microsoft tulkitsee mielenkiintoisesti Azure AD -palvelussaan OpenId Connect -tunnistamisessa id_tokenissa luovutettavan iss claimin merkityksen.
On vaikea perustella saati väittää…

